# Contents [Networking Model](#/model) [Physical Layer](#/physical) [Physical layer attacks](#/attacks)
# Networking Model
## OSI model - "Open Systems Interconnection" model, developed starting in 1977 - Everybody (including many textbooks!) uses the OSI model diagrams (see next slide), and talks about TCP/IP - But they are not the same! - TCP/IP does not fit perfectly into the OSI model - We don't care too much about the differences here, so we'll do that as well - See [here](http://en.wikipedia.org/wiki/OSI_model#Comparison_with_TCP.2FIP) for details ## OSI Model [](https://commons.wikimedia.org/wiki/File:OSI_Model_v1.svg) ## TCP/IP Model [](https://commons.wikimedia.org/wiki/File:OSI_Model_v1.svg) <!-- .slide: class="right-float-img-800 no-border" --> ## Protocol stack: physical layer [](https://commons.wikimedia.org/wiki/File:Ethernet_cable._SAM.jpg) - Is charged with getting data<br>from one end of the 'wire'<br>to the other end - Examples: - copper wire - fiber optic cable - wireless transmission<br>(WiFi, Bluetooth, satellite<br>communication), etc. ## Protocol stack: data link layer <!-- [](https://commons.wikimedia.org/wiki/File:Ethernet_Connection.jpg) --> <img src="http://www.cs.virginia.edu/~asb2t/duimg/n01/image9.png" style="height:300px"> - Is charged with getting one packet of data from one host to another connected host - Via the next layer down - Most common example is Ethernet - Other examples: ARP, ISDN, PPP, ATM, FDDI, SONET, SDH, etc. ## Protocol stack: network layer <!-- [](https://commons.wikimedia.org/wiki/File:Sprouter100g.jpg) --> <img src="http://www.cs.virginia.edu/~asb2t/duimg/n01/image8.png" style="height:300px"> - Is charged with *routing* a *single* packet of data from one computer to another (via the next layer down) - In TCP/IP, called the "Internet" or "Internet Protocol" (hence "IP") layer - Example protocols: IP, ICMP (used for 'ping'), IPsec (for VPNs) <h2 class="r-fit-text">Protocol stack: transport layer</h2> <img src="http://www.cs.virginia.edu/~asb2t/duimg/n01/image7.png" style="height:300px"> - Is charged with taking a large piece of data, splitting it into smaller packets, sending each packet to the destination (via the next layer down), and (maybe) reassembling it at the destination - It might request a missed packet to be re-sent - Example protocols: TCP, UDP ## Protocol stack: session & presentation layers - Are charged with such tasks as managing network sockets, compressing/encoding/ encrypting the data, etc. - These layers do not exist in the TCP/IP model! - This functionality is included in the TCP/IP application layer - Example protocols: TLS, SSL, NetBIOS <!-- .slide: class="right-float-img-800" --> ## Protocol stack: application layer  - Is the top-level protocol used to communicate to the application on the other end - Example protocols: DHCP, DNS, FTP, HTTP, IMAP, NTP, POP, SMTP, SSH ## Network device terminology - Node: any device on a network - Switch: a node that connects networks on the *data link layer* only - Also called a bridge - Router: a node that connects networks on the *network layer* - Gateway: a node that connects two networks that (potentially) use different protocols - Also translates addresses, etc. - Firewall: blocks 'bad' traffic (more on this in a few slides) ## How a packet travels  - Note that routers connect more than 2 wires - Otherwise itʻs a gateway ## Packets in packets <img src="http://www.cs.virginia.edu/~asb2t/duimg/n01/image6.png#stretch" class="stretch"> ## Firewall - A firewall prevents unrequested network connections from outside hosts - Typically part of a residential 'gateway' or 'router' - It isolates the 'inside' network and the 'outside' network - If you request data (a http connection), the sent data is then 'requested' data, and is allowed to pass through - You can 'poke a hole' in a firewall to allow access to a certain port (such as ssh)
# Physical Layer
<!-- .slide: class="right-float-img-800 no-border" --> ## Protocol stack: physical layer [](https://commons.wikimedia.org/wiki/File:Ethernet_cable._SAM.jpg) - Is charged with getting data from one end of the 'wire' to the other end - Examples: - copper wire - fiber optic cable - wireless transmission (WiFi, Bluetooth, satellite communication), etc. ## Copper Wire Evolution <a href='https://commons.wikimedia.org/wiki/File:BNC_connector_with_10BASE2_cable-92170.jpg'><img src="https://upload.wikimedia.org/wikipedia/commons/thumb/7/74/BNC_Tee_connector_for_10BASE2-92165.jpg/1024px-BNC_Tee_connector_for_10BASE2-92165.jpg" style="float:left;height:300px" class="no-border"></a> <a href='https://commons.wikimedia.org/wiki/File:BNC_Tee_connector_for_10BASE2-92165.jpg'><img src="https://upload.wikimedia.org/wikipedia/commons/thumb/5/5f/BNC_connector_with_10BASE2_cable-92170.jpg/1024px-BNC_connector_with_10BASE2_cable-92170.jpg" style="float:right;height:300px" class="no-border"></a> <br clear='all'> - Early Ethernet used co-axial cable - Only 2 wires, one ground and one data - Multiple devices on the same network could have their data *collide* - Called 10base-2 <!-- .slide: class="right-float-img-800 no-border" --> ## Copper Wire Evolution [](https://commons.wikimedia.org/wiki/File:Ethernet_RJ45_connector_p1160054.jpg) - Modern Ethernet uses 10-base/T - 8 wires, twisted in pairs - Separate pairs for each direction ## Copper Wire Evolution - Various manufacturing qualities determine maximum speed [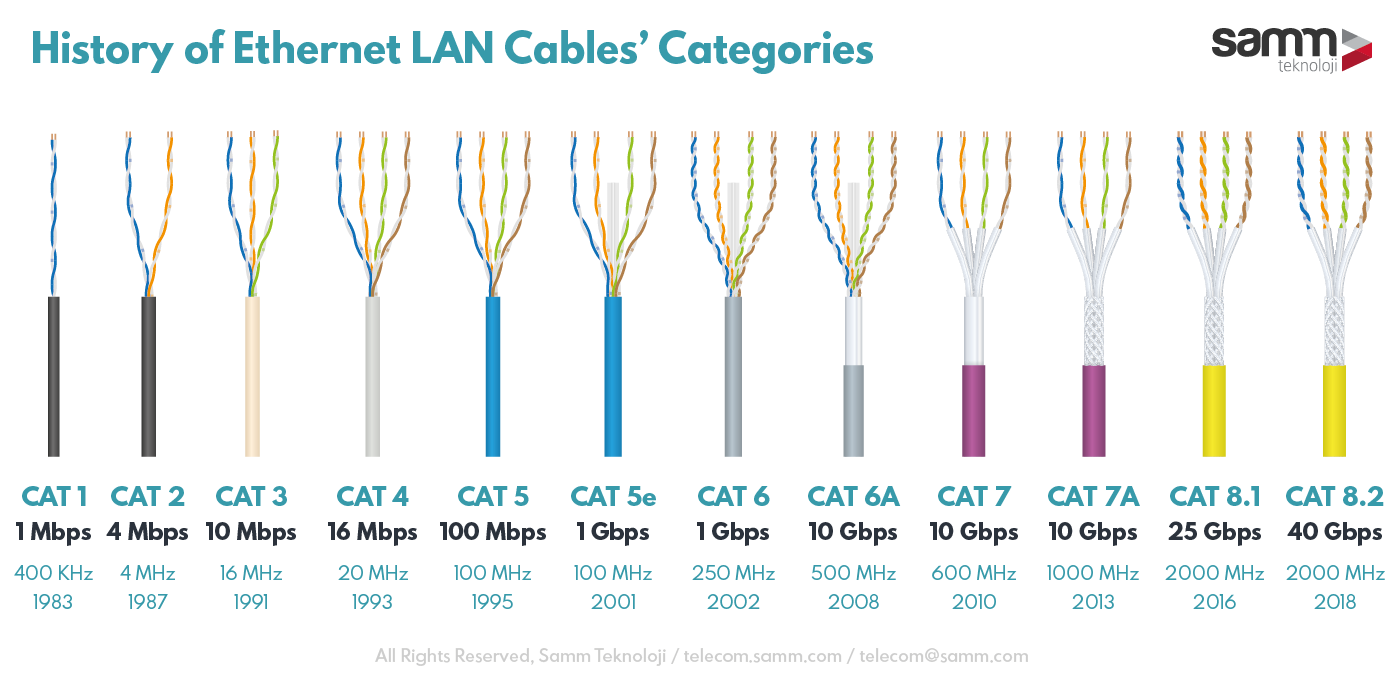](https://telecom.samm.com/history-of-ethernet-lan-cables-categories) <!-- .slide: style="width:1200px;margin-left:-100px;font-size:smaller" --> ## Speed Comparison | Type | Year | Speed<br>(Mbit/s) | 10 Gb<br>download | Aliases | |----|----|----|---|---| | 10base-2 | 1983 | 10 | 2h, 13m, 20s | | 100base-T | 1995 | 100 | 13m, 20s | fast Ethernet | | Comcast avg | N/A | 236 ([ref](https://www.cnet.com/home/internet/xfinity-speed-test-results/)) | 5m, 38s | | 1000base-TX | 1999 | 1000 | 1m, 20s | gigabit Ethernet | | 10Gbase-T | 2006 | 10,000 | 8s | 10 gigabit Ethernet | | 40G fiber | 2007 | 40,000 | 2s | | 802.11b wi-fi | 1999 | 11 | 2h, 1m, 12s | Wi-Fi 1 | | 802.11g wi-fi | 2003 | 54 | 24m, 41s | Wi-Fi 3 | | 80211n wi-fi | 2014 | 600 | 2m, 13s | Wi-Fi 4 | | 80211ac wi-fi | 2014 | 6,933 | 11s | Wi-Fi 5 | <!-- .slide: class="right-float-img-600 no-border" --> ## Early Ethernet: Hub [](https://commons.wikimedia.org/wiki/File:4_port_netgear_ethernet_hub.jpg) - A *hub* connects devices on the same shared network - Basically a soldering of the wires together - Creates the topology on the previous slide - Collisions happen quite often - They haven't been sold since the 1990's - Replaced by swithces <!-- .slide: style="width:1200px;margin-left:-100px;font-size:smaller" --> ## Wifi Speed Comparison Speeds have improved over time | Type | Year | Speed<br>(Mbit/s) | 10 Gb<br>download | Aliases | |----|----|----|---|---| | 802.11b wi-fi | 1999 | 11 | 2h, 1m, 12s | Wi-Fi 1 | | 802.11g wi-fi | 2003 | 54 | 24m, 41s | Wi-Fi 3 | | 80211n wi-fi | 2014 | 600 | 2m, 13s | Wi-Fi 4 | | 80211ac wi-fi | 2014 | 6,933 | 11s | Wi-Fi 5 | ## Wi-Fi encryption - This encrypts all data sent over a wireless network - This encryption is done at the network or data-link level - Application-level encryption (https, ssh, imaps, etc.) is on top of Wi-Fi encryption - We will see wireless security later this semester
# Physical Layer Attacks
## Physical attacks - Plug an Ethernet cable into a hub (or switch), and you have access (probably) to the network - Cut the wires, and you have caused network problems - Send high voltages through the Ethernet cables to short out the network devices - Send interference on the wifi channels to block other devices from connecting - Yank the hard drive and image it - Encryption would block this - Lots of wifi attacks, which we'll see later <!-- .slide: class="right-float-img-800 no-border" --> ## Plunder Bug LAN Tap  - Available [here](https://hak5.org/products/bug) for $80 from [hak5.org](https://hak5.org) - Network monitoring and recording via a USB-C port - There is another network port on the end not visible in the picture <!-- .slide: class="right-float-img-800 no-border" --> ## Packet Squirrel  - Available [here](https://hak5.org/products/packet-squirrel-mark-ii) for $100 from [hak5.org](https://hak5.org) - It intercepts network packets, and can pass them to the USB-connected computer - Also has a network jack on the far end - Can perform network manipulation, monitoring, and various attacks <!-- .slide: class="right-float-img-800 no-border" --> ## LAN turtle  - Available [here](https://hak5.org/products/lan-turtle) for $80 from [hak5.org](https://hak5.org) - Discrete network access; looks like an Ethernet adapter - Chip inside can perform MITM attacks, scan networks, manage remote access, etc. <!-- .slide: class="right-float-img-800 no-border" --> ## USB Rubber Ducky  - Available [here](https://hak5.org/products/usb-rubber-ducky) for $80 from [hak5.org](https://hak5.org) - Looks like a USB flash drive - Appears to the computer as a keyboard - Some pre-set commands come built in - You have it "type" custom commands - Technically not a network attack <!-- .slide: class="right-float-img-800 no-border" --> ## Bash Bunny  - Available [here](https://hak5.org/products/bash-bunny) for $120 from [hak5.org](https://hak5.org) - Has a series of pre-programmed exploits to try on whatever computer it is plugged into - LED light turns green when one works - Technically not a network attack <!-- .slide: class="right-float-img-600 no-border" --> ## USBKill  - Available [here](https://usbkill.com) for `$`56 to `$`145, depending on the model - A high Farad capacitor that charges from the USB port - Then shoots that power back into the machine, likely frying it - Technically not a network attack <!-- .slide: class="right-float-img-800 no-border" --> ## Defenses  - Only three of these attacks do *physical* damage: - The electrical surge over the Ethernet wire - [This $16 device on Amazon](https://www.amazon.com/dp/B00UYXRDU8) can protect against this - Cutting the network wires - Block physical access to all unauthorized individuals - USBKill - Block physical access to all unauthorized individuals - The other attacks allowed physical access for a software attack