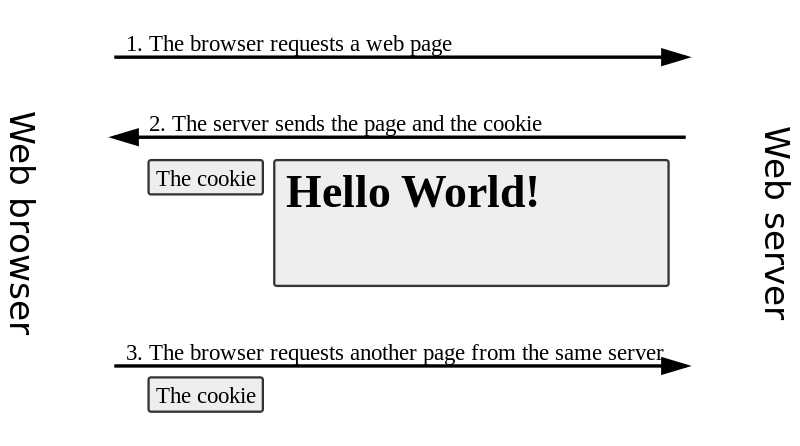
2. Cross-domain content
- Website A can include an image (or script, or CSS file) from website B
- Now both A and B can leave cookies
- This request includes the referring website! So B can see where you have been
- Part of the headers of any Stack Overflow page:
- So Google now knows what sites you’ve visited
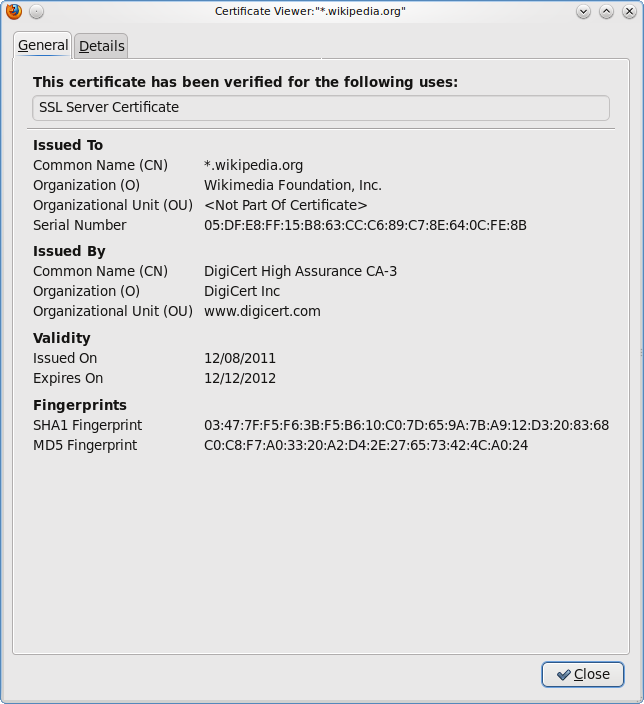

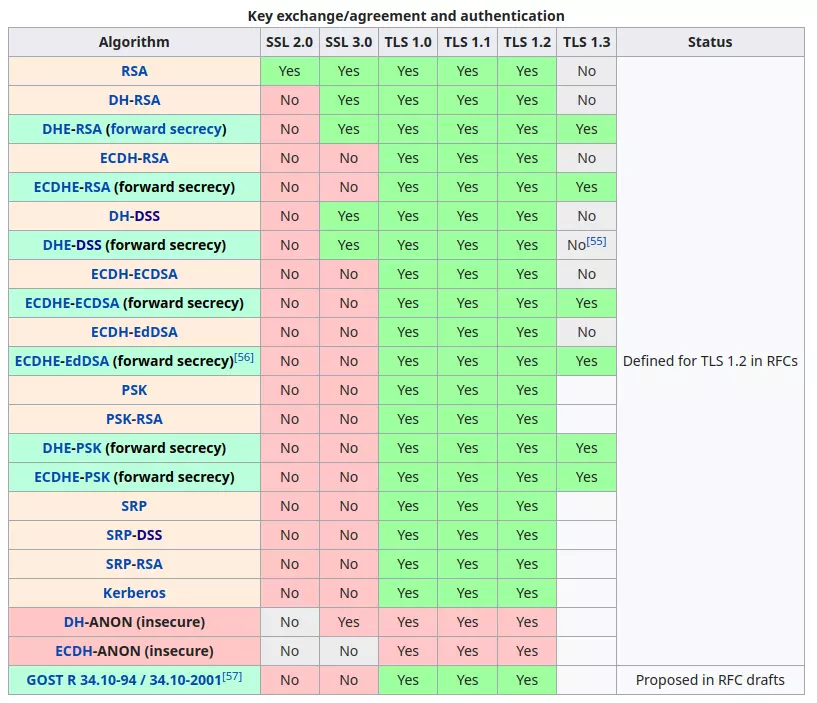
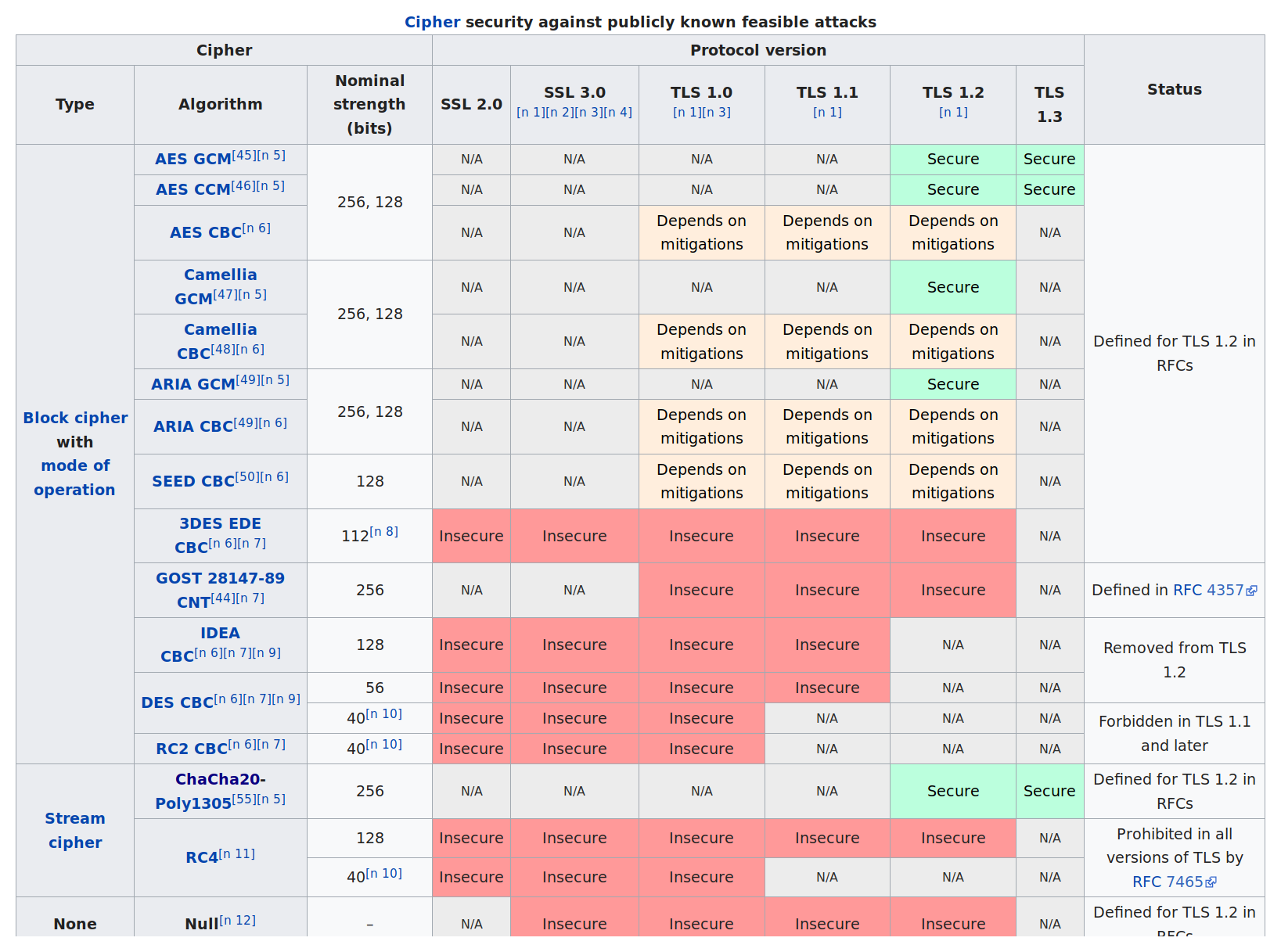
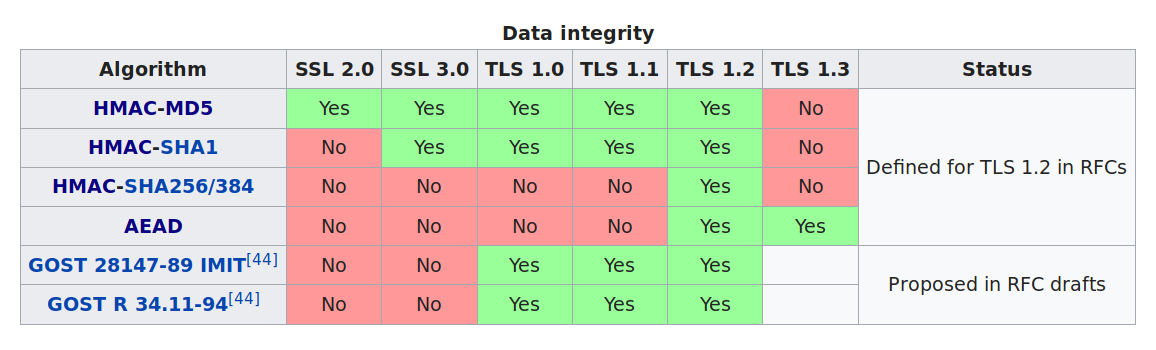 Note that even if the MAC doesn’t support encryption (in the first 3 rows), the cipher (likely AES) still does
Note that even if the MAC doesn’t support encryption (in the first 3 rows), the cipher (likely AES) still does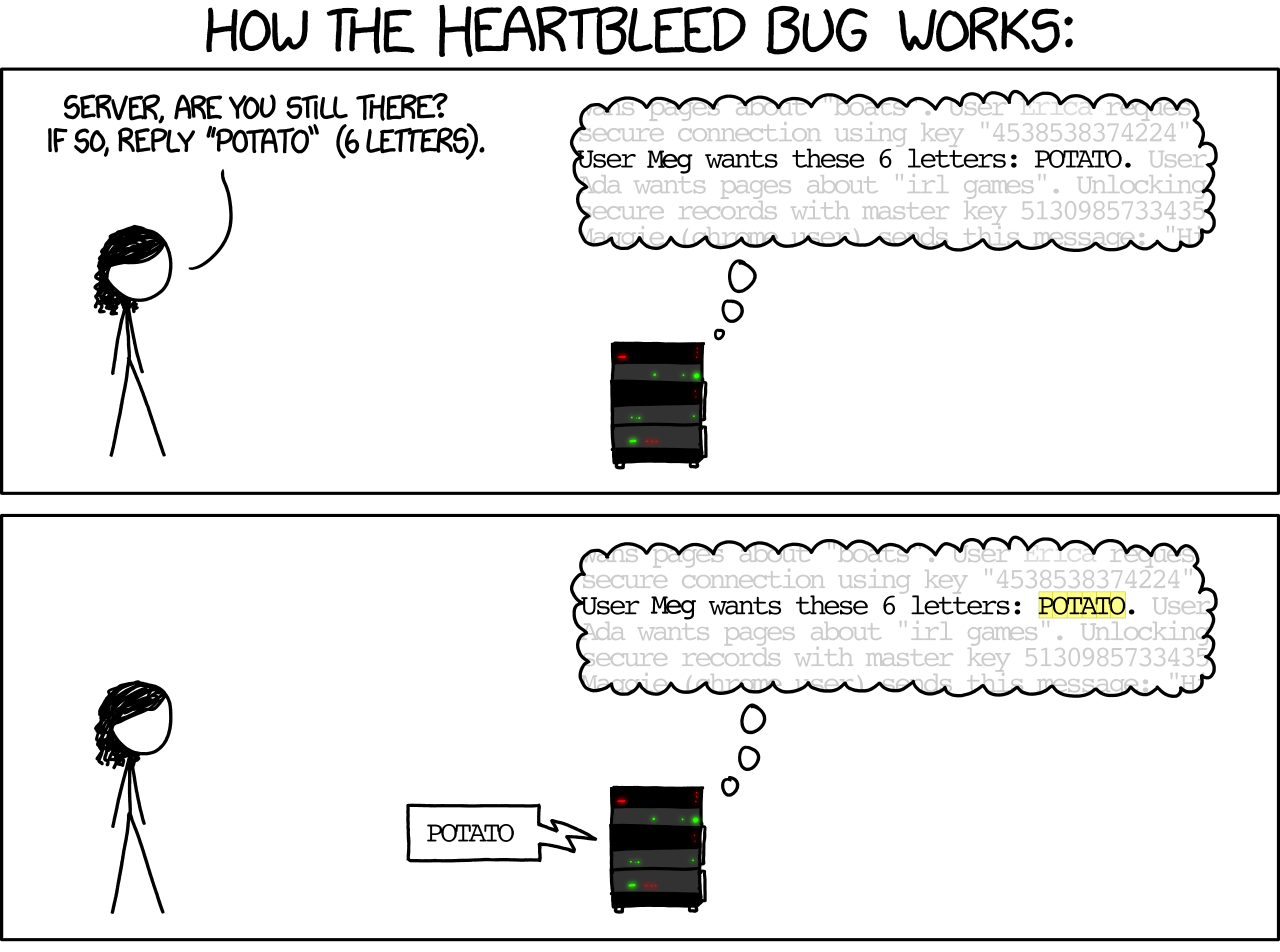
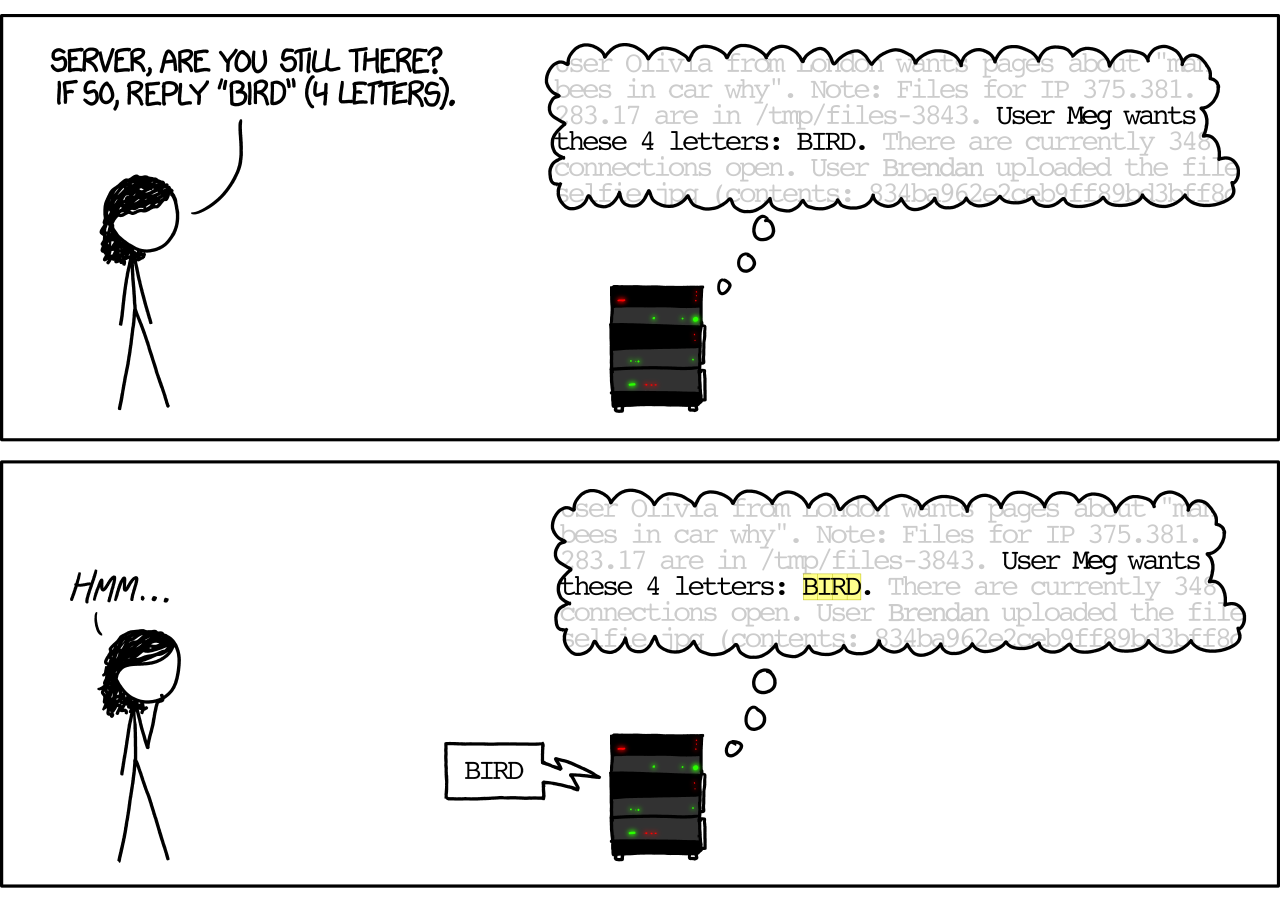
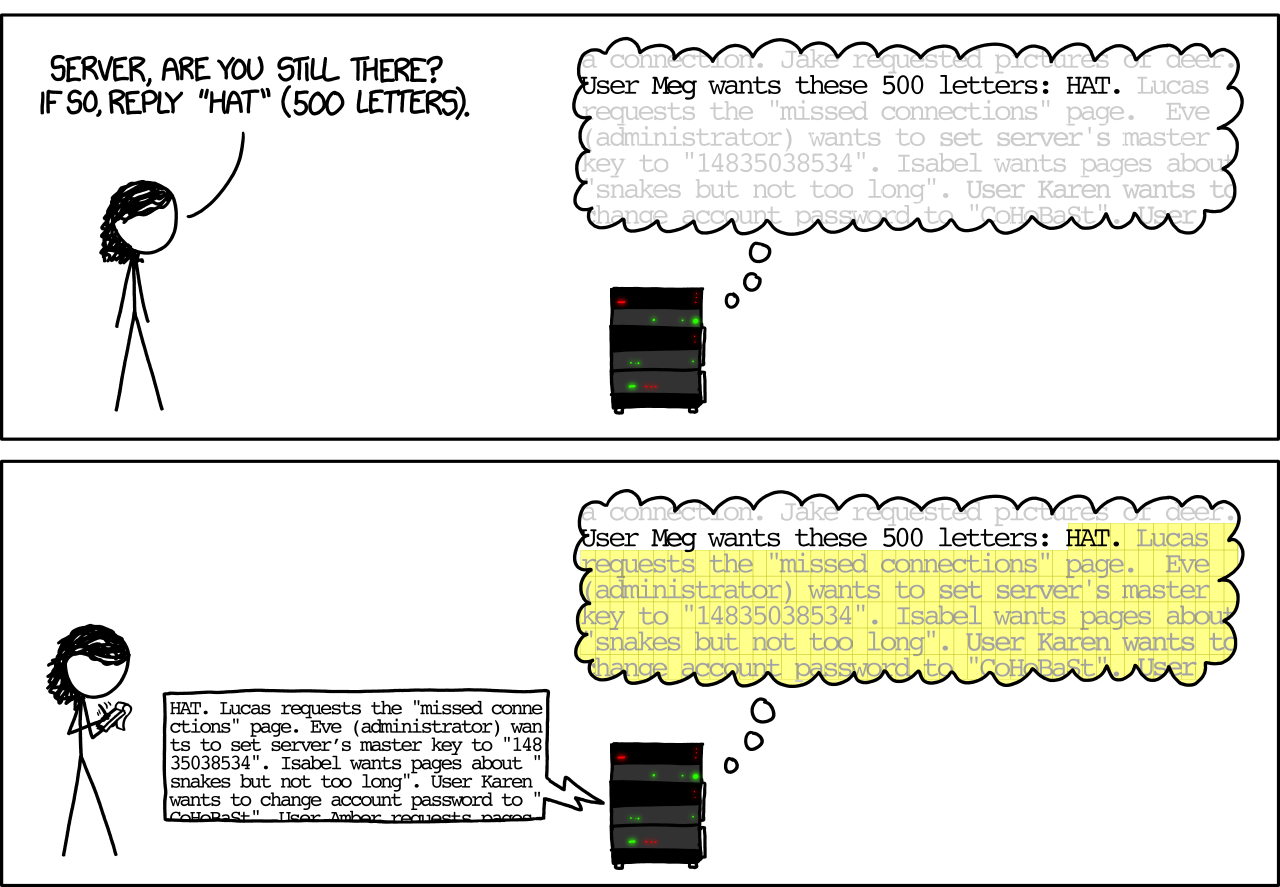



4. Social media comment boxes