CS 3710
Introduction to Cybersecurity
Aaron Bloomfield (aaron@virginia.edu)
@github | ↑ |
Virtual Machines
History
Hardware utilization
- During the 1960s and 1970s
- IBM VM/370 operating system
- Hypervisor (control program) creates virtual machine environment
- Each user has own virtual machine with guest OS, own address space, virtual devices, etc.
- Hypervisor (control program) creates virtual machine environment
Decline
- In the 1980s and 1990s, VMs decline in popularity
- Poor performance
- Client-server applications
- Inexpensive PCs
- Distributed computing
- VMs started as mainframes (one computer for the entire company)
- Then cheap PCs showed up
Renewed Interest
- In the late 1990s
- Issues/Challenges
- Low Infrastructure Utilization
- Physical infrastructure costs
- IT management costs
- Failover/disaster protection
- High maintenance end-user desktops
Renewed Interest cont’d
- Issues to resolve…
- Software compatibility
- Isolation capability
- Encapsulation
- Low overhead/high performance
Concepts
Virtual machine types
- Language level
- Example: Java Virtual Machine
- Process level
- Example: Wine
- Operating System level
- Example: Docker, BSD jails
- System level
- Example: VirtualBox, VMware, Hyper-V
Terminology
- Host OS: the operating system that booted the computer
- Guest thing: what is being run in the virtual machine
- Here, thing could be a process, operating system, etc.
Language virtual machine
- The Java Virtual Machine is a classic example
- Compiler translates .java files to bytecode (.class) files
- Any interpreter is really a language virtual machine
- Python, Ruby, PHP, etc.
- The interpreter / langauge VM can:
- Handle memory issues (including garbage collection)
- Do lots of error checking and tracing
- Still be reasonably fast
JVM diagram
 From here
From here
Process virtual machine
- Allows one to run a single process
- Meant to provied a platform independent environment for a process to run
- Abstracting away things like the hardware, host OS, etc.
- Wine (Windows emulator for Linux) is an example
- The binary executes, but Windows system calls are translated into Linux system calls
- A library (Winelib) fills in for Windows system calls that do not have Linux equivalents
Process VM examples
- Multiprogramming
- Each user process given the illusion of having complete machine to itself
- OS supporting multiple user processes
- Each user process given the illusion of having complete machine to itself
- Emulators and dynamic binary translators
- Emulate one instruction set on hardware designed for different instruction set
- Dynamic binary translation: convert blocks of source instructions to target instructions that perform equivalent functions
Process VM Examples (cont’d)
- High-level language VMs
- Cross-platform portability
- Minimize hardware-specific and OS-specific features
- Java VM
- So one can argue that a language VM is really a process VM…
- But we’ll differentiate them
OS virtual machine
- The host OS shares the same kernel with all the guest OSes
- But each guest OS has its own memory space
- This separates the different guest OSes from each other and the host OS
- First implementation was FreeBSD jails; Linux’s first implementation was LXC
- Most common known example now is Docker
OS virtual machine
- FreeBSD jails are a first-class concept in an OS
- Meaning something the OS directly supports and implements
- Containers are not
- They are built from other first-class concepts (namespaces, cgroups, etc.)
- That means you can do more, but there are more bugs and complexity
- See jfrazelle’s blog post for more
OS VM examples
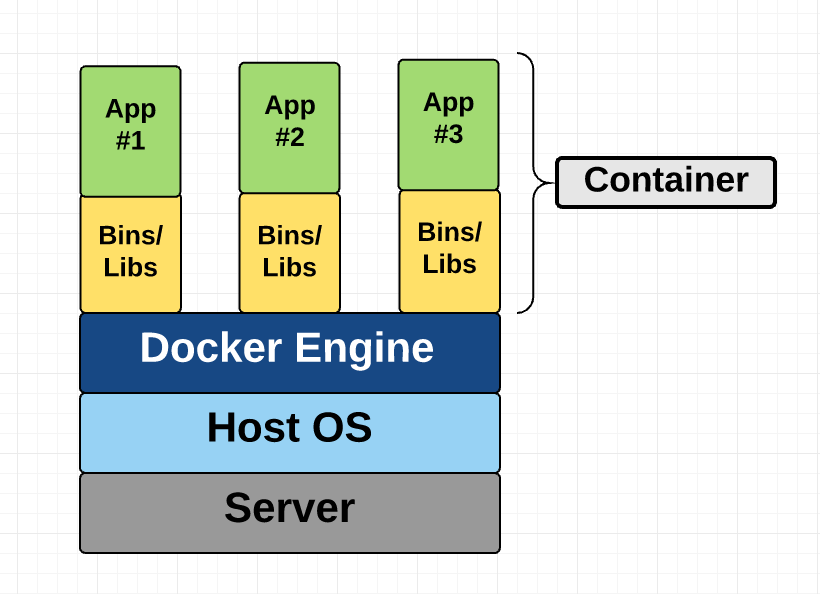
- Docker is popular
- Also LXC, LXD
- FreeBSD jails
- Solaris Zones
Image from here
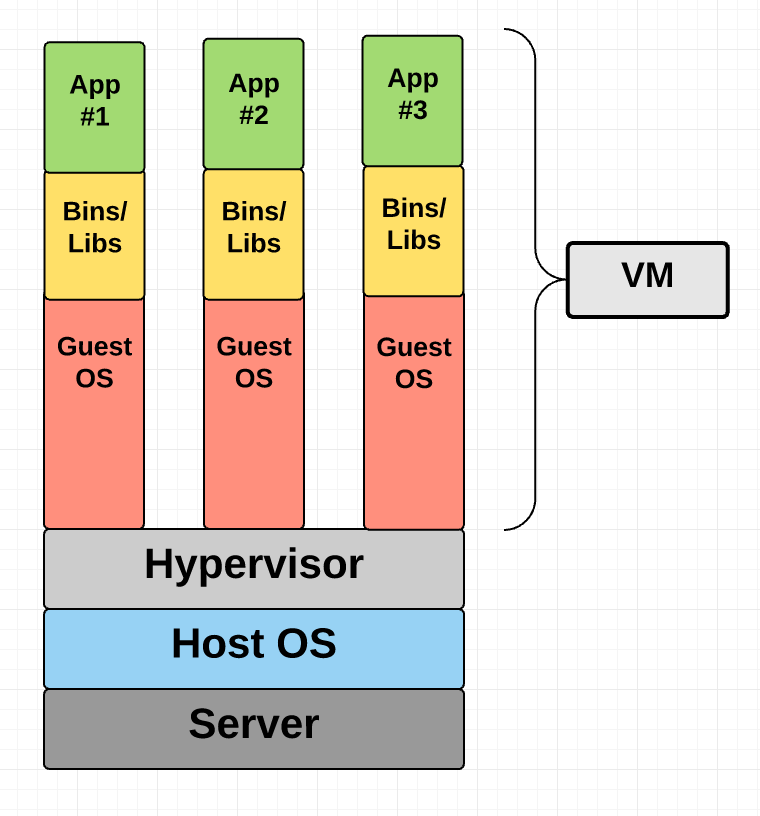
System virtual machine
- Designed to emulate “real” hardwre
- Presents hardware, not drivers, to the guest
- Whereas the other VMs will present network connections to the guest, a system VM will present an Ethernet device
- Likewise, not memory allocation calls, but page tables
- These run entire operating systems, and take the most resources
- VirtualBox is the example we all know and love
- VMWare is popular; Hyper-V is for Windows
System VM examples
- Classic system
- Virtual machine monitor (VMM) on bare hardware
- IBM VM/370
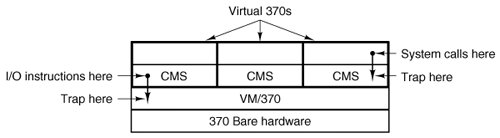
Image from here
System VM examples
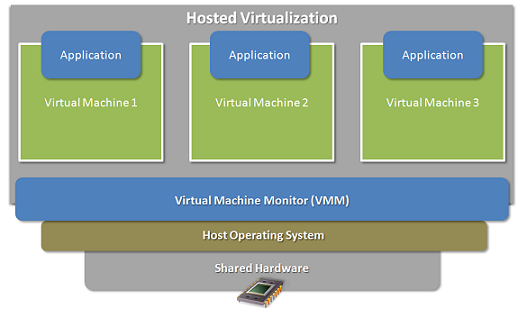
- Hosted VM
- VM runs on OS
- VMWare, VirtualBox
Image from here
System VM examples (cont’d)
- Whole System VMs (Emulation)
- Complete software system (OS and applications) supported on a host system running a different ISA and OS
- VirtualPC (Windows on Mac)
- Complete software system (OS and applications) supported on a host system running a different ISA and OS
- Codesigned VMs (Hardware optimization)
- No native applications; VM software is part of hardware implementation
- Transmeta Crusoe
- No native applications; VM software is part of hardware implementation
Terminology confusion
- Some will eliminate OS level, since that’s just process level on steroids
- Others will combine language level and process level, since they are both for a single process
- Wikipedia VM article does this
Virtualization
- Formally:
- Virtualization involves the construction of an isomorphism that maps a virtual guest system to a real host. (Popek and Goldberg, 1974)
Virtualization
- Mapping of virtual resources or state to real resources on underlying machine
- E.g., registers, memory, files
- Emulation of the virtual machine ABI or ISA
- ABI: Application Binary Interface: how an executable interacts with a library or the OS
- Use of real machine instructions and/or system calls to carry out actions specified by virtual machine instructions and/or system calls
ABI vs API
 From wikipedia
From wikipedia
VM Operations
OS refresher
- User programs run in user mode
- Where a crash (segfault) will kill the process, but not the entire OS
- Programs are restricted in what they can do
- They can’t directly access hardware; they have to go through the OS
- The OS itself runs in kernel mode
- Where a crash will, in fact, crash the entire OS
User mode vs Kernel mode
- Boundary is defined by:
- System calls
- Called by user-mode programs, but the function body is completed in kernel mode
- Device drivers
- Code written by somebody other than the OS writer, but runs in kernel mode
- (whether they are in kernel mode fully or not varies by OS)
- System calls
User mode vs Kernel mode
- If a guest OS tries a priviledged operation:
- The VM forwards to the VMM
- VMM: Virtual Machine Monitor
- The VMM handles it by a system call if possible
- But it’s in kernel mode, so it can do it directly
- The VM forwards to the VMM
VMs and kernel mode
- VMs tend to run the guest OS in user mode
- But the OSs think they are running on hardware, so they will attempt to do “priviledged” things (like access hardware directly)
- The Virtual Machine Monitor (VMM) handles this
- It is tyipcally a device driver running in kernel mode
- Exceptions from the OS are passed, through the VMM, back to the VM
VMM diagram
Image from here
Abstraction
Levels of Abstraction
- Allow implementation details at lower levels of a design to be ignored or simplified
- Arranged in a hierarchy
- Lower levels - Hardware
- Physical components with real properties
- Higher levels - Software
- Logical components
- Lower levels - Hardware
Levels of Abstraction: HW/SW Interface
- High level language (HLL) -> Assembly language
- Compiler (translation)
- Assembly Language -> Operating System
- Assembler (translation/mapping to ISA)
- Operating System -> Instruction Set Architecture (ISA)
- Partial Interpretation (device drivers, etc)
- Instruction Set Architecture -> Digital logic
- Hardware
- Digital logic -> Electronics (transistors, etc.)
- Hardware
Levels of Abstraction: Java
- Java (HLL) -> Java Byte Code (ISA)
- Java Compiler
- Java Byte Code (ISA) -> Java Virtual Machine (JVM)
- Interpreter and JIT compiler
- Java Virtual Machine (JVM) -> OS
- Machine ISA
Well-defined Interfaces
- Decouple design tasks
- Instruction set
- Intel and AMD
- IA-32 instruction set
- Compilers
- Map high level language to ISA
- Intel and AMD
- Operating system interface
- Application development
- Instruction set
Well-defined interfaces: Challenges
- Reduced interoperability
- Processors support limited instruction sets
- IA-32 vs. PowerPC
- Different operating systems
- Windows vs. Linux
- Application binaries
- Dependent on OS and instruction set
- Processors support limited instruction sets
- Hardware resource considerations
- OS
VM Examples
Hosted VM: VMWare

VMWare Workstation
- Virtual machine software suite for x86 and x86-64 computers
- Supported host OS’s
- Windows and Linux
- Supported guest OS’s
- Over 200 supported
- Windows, Linux, BSD variants
- Allows one physical machine to run multiple operating systems simultaneously
VMWare Workstation
- Uses bridging to provide mapping to
- Network adaptors
- CD-ROMs
- Hard disk drives
- USB devices
- Simulation capability for some hardware
- Mounting ISO as CD-ROM
- Mounting .vmdk files as hard disks
VMWare Workstation
- Snapshot functionality
- Enables rollback to saved status
- VMWare Tools
- Package with drivers and other software that can be installed in guest operating systems to increase their performance
- Drivers for emulated hardware
- Drag and drop file support
- Clipboard sharing between host and guest
VMs and Malware
Why do we care about VMs?
- We can run malware within them to ‘sandbox’ them
- This allows pausing the execution at various points
- We can simulate other architectures / software systems to study malware
- If we are trying to “break” things, that “breaking” is contained
- Experimenting with
fork()for example – we don’t want to fork bomb our host machine
- Experimenting with
But are you in a VM?
- Meta-question: are you living in a computer simulation
- We’ll leave that question for the philosophy classes…
- In Linux, you can install and run
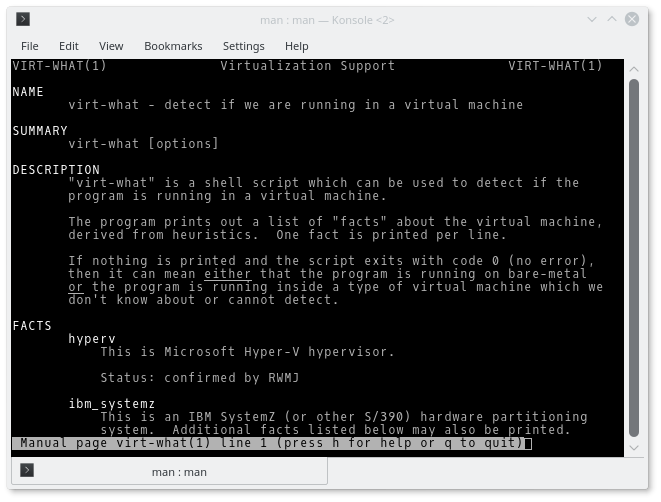
virt-what, which will determine if you are in a VM or not
virt-what
VM Security
- Docker is known to be rather insecure
- Containers use the same OS, so a kernel bug will exist in both
- There have been “break-outs” of system VMs as well
- One from March 2017
VM Break-out
 Article is here
Article is here